A practical guide to integrating the captive portal with the PMS without disrupting the guest experience
How to design an effective integration between the captive portal and the hotel PMS: technical architecture, real-time validation, security, data synchronisation and guest verification. A practical approach to improving data quality and operational efficiency.
Although the hotel’s WiFi and PMS work with the same guest information, in practice they often operate independently. Integrating them not only improves data accuracy, but also reduces manual tasks and operational errors.
In many of our meetings with IT team managers (hotel technology and systems), they tell us that they have implemented a modern captive portal to provide WiFi to guests, keeping detailed records within the PMS, often manually. The problem is that the two systems operate independently.
For example, companions travelling with the main contact on the booking never appear in the CRM databases, and manually collected emails often contain error rates of over 30%, damaging the sender’s reputation and limiting the effectiveness of email marketing campaigns.
The solution is to redesign the path that guest data must take: how it goes from WiFi access to validation in the PMS and, finally, to personalisation in the CRM.
The most advanced hotel groups have moved away from isolated systems. Today, they integrate the captive portal with the PMS to validate guests, identify companions, and ensure that only reliable data reaches their marketing tools.
Thanks to this integration, data capture no longer depends on manual processes and moves to an automated flow that validates between 70% and 80% of records, also guaranteeing 99% email deliverability in marketing campaigns.
The blind spot of WiFi in hotels: how thousands of guest records are lost every month
In most hotels, the WiFi network is managed with a basic authentication model that leaves large gaps in guest data collection. The process is often limited to a simple web form: the customer enters their name or email address and gains immediate access, with no connection to the PMS records. This approach turns WiFi into a simple browsing service, rather than leveraging it as a strategic touchpoint to validate information, identify companions and enrich the hotel’s database from the outset.
The technical architecture of most establishments exacerbates this problem by isolating the system. Captive portals operate independently of the PMS, with no real-time communication between guest authentication and booking verification. When guests provide their name and email address to access WiFi, the system has no mechanism to confirm their identity with PMS records or detect discrepancies that indicate data entry errors.
This isolation also means that data on the guest’s companions is not collected. In many countries, companions do not provide registration information at reception, which means that their data will never be entered into the PMS.
Traditional captive portals capture information from these companions during the WiFi login process, but they have no mechanism for associating this data with the main booking or updating guest profiles in the PMS. The result is fragmented data that only exists in the WiFi logs, rather than enriched guest records.
Real-time validation: how the PMS ensures that every WiFi log is reliable
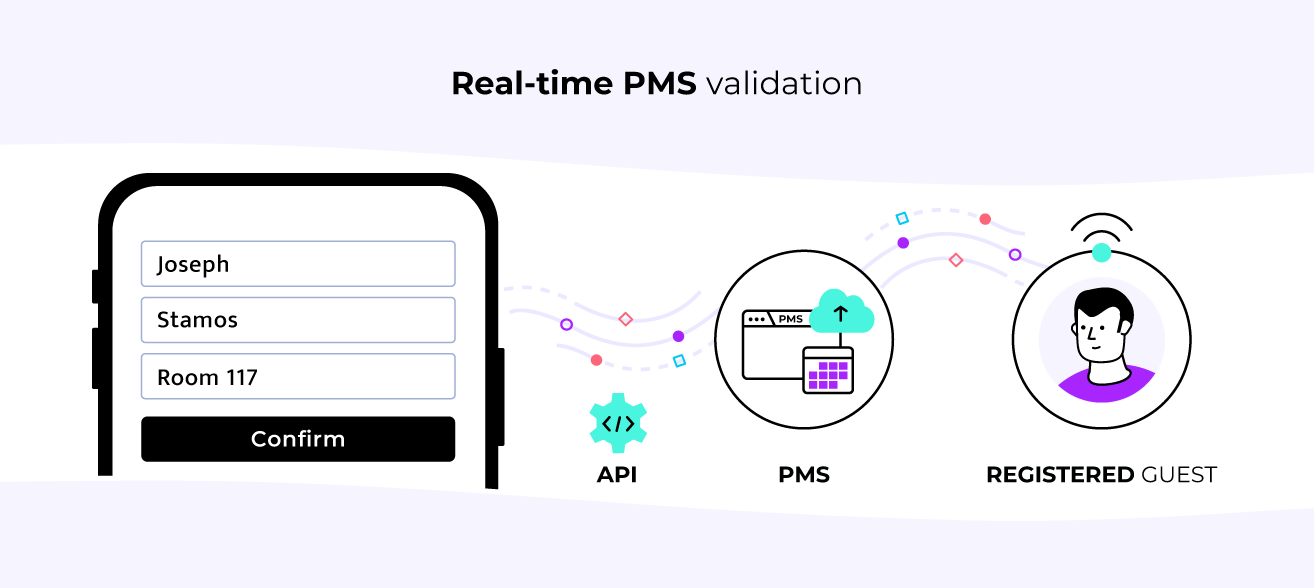
Advanced captive portal implementations integrate directly with the PMS to validate guest identities and enrich real-time data collection.
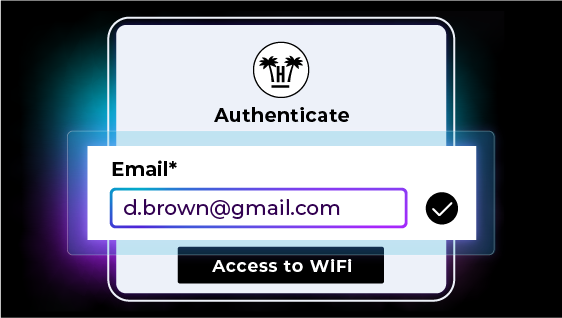
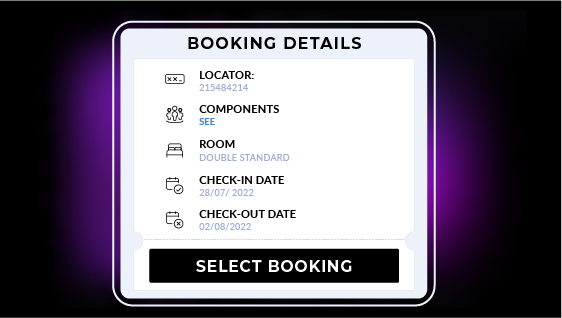
When a customer attempts to connect to the WiFi, they enter their first name, last name, and room number. The captive portal instantly verifies this information against active PMS records through API integration. This process confirms that the person requesting network access is indeed a registered guest at the property.
On a technical level, the integration is based on the configuration of API connection points between the captive portal and the PMS, protected by authentication protocols that ensure reliable and private data exchange. The validation process typically takes between 200 and 500 milliseconds, providing an almost instantaneous response without causing any noticeable delays in the WiFi connection.
Intelligent matching algorithms correct common discrepancies that arise when entering data manually. The system recognises reversed first and last names, differences in accents or capitalisation, and minor typos that would otherwise block validation. When an exact match is not detected, the algorithm identifies partial matches and suggests options to confirm the guest’s identity, reducing friction and preserving data accuracy.
Automated guest capture: the hidden value of PMS integration with the captive portal
The greatest opportunity offered by the integration between the captive portal and the PMS lies in the information that is normally lost: companions. While traditional methods barely register the booking holder, advanced systems automatically capture the data of all guests connected to the Wi-Fi, updating or creating their profiles in the PMS using the integration API.
This eliminates the information gaps that manual processes cannot systematically cover.
The technical flow begins when a companion attempts to authenticate themselves on the Wi-Fi network. The system requests basic data such as name, email address and room number, and validates this information with the records in the PMS. Once the relationship with an active reservation is confirmed, the captive portal creates a new profile or updates an existing one with the companion’s data.
The API automatically manages the association between guests and the main booking, maintaining the correct structure within your system. This allows you to link multiple guests to the same stay, record family or group relationships, and ensure that marketing preferences and consent are applied individually.
This automated approach typically increases the total amount of guest data by 40% to 60% compared to traditional methods.
Control mechanisms that prevent incorrect data entry
Real-time email verification is one of the most critical technical components in integrating the PMS with the captive portal. Instead of cleaning databases after poor-quality data has already entered marketing systems, advanced implementations verify email addresses within milliseconds of immediate entry and prompt guests to correct errors before completing WiFi authentication.
The verification process operates across multiple technical layers that check different aspects of email validity.
- Syntactic validation ensures that email addresses follow proper formatting rules and contain the necessary elements, such as the @ symbol and domain extension.
- Domain validation confirms that the email domain exists and has correctly configured mail exchange records that can receive messages.
- Disposable email detection identifies temporary email services that guests might use to avoid providing real contact information.
Advanced verification systems also detect spam traps, blacklisted domains, and role-based email addresses that indicate business accounts rather than personal ones. When verification fails, the system provides immediate feedback with specific error messages that help guests understand what they need to correct. This real-time approach prevents poor-quality data from entering the system, while maintaining a smooth user experience.
To function properly, the system must connect the captive portal with external verification services, manage potential delays or interruptions, and ensure that the guest’s experience when accessing WiFi remains immediate.
The four stages to achieving full integration between PMS and WiFi
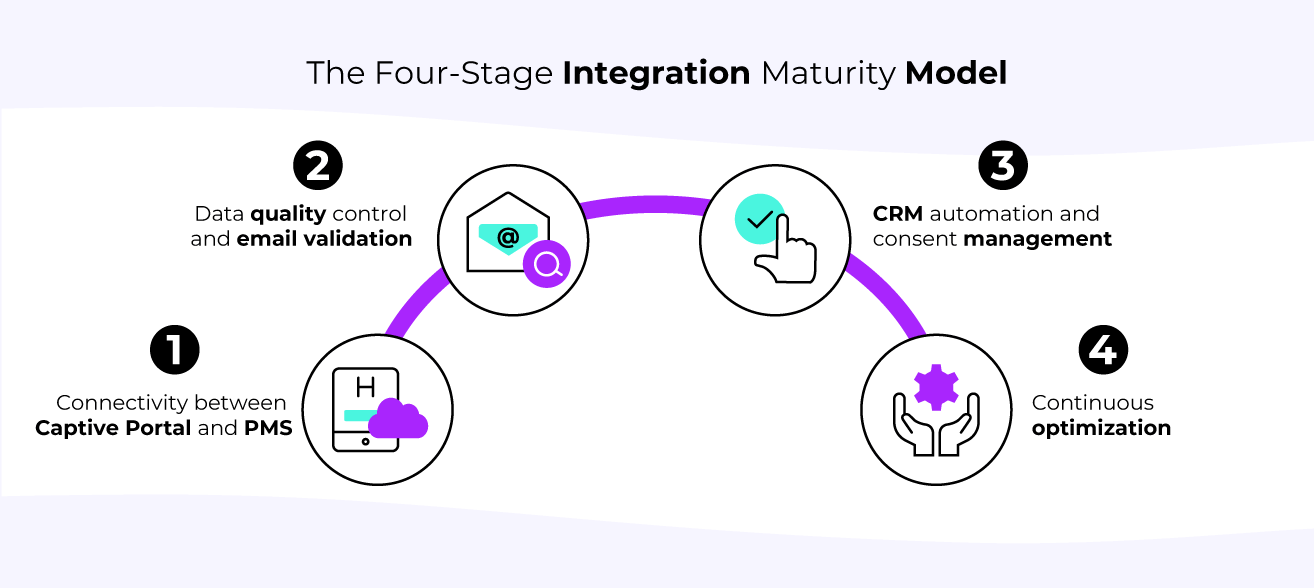
Hotel groups implementing captive portal PMS integration typically go through four distinct stages of maturity, each building on the technical capabilities and operational processes established in the previous phases. Understanding this progression helps IT teams plan implementation roadmaps and set realistic expectations for system capabilities and business outcomes.
Stage One: Basic connectivity between the captive portal and the PMS.
The integration validates guest identities against property management records and provides immediate feedback when authentication fails. This foundation eliminates most WiFi access issues while establishing the technical infrastructure for more advanced data collection and verification processes.
Stage two: real-time email verification and complementary data capture.
The system begins to collect comprehensive guest information and implement quality controls that prevent poor-quality data from entering downstream marketing systems. Operational processes are adapted to handle the increased volume and quality of data, and staff training focuses on serving guests through the enhanced authentication process.
Stage three: integrate CRM and automate consent validation, consolidating guest data into a single environment.
Guest data flows automatically from the captive portal, through PMS validation, to the CRM, without manual intervention. The system manages GDPR compliance requirements, consent logging, and preference management, while maintaining audit trails for regulatory compliance.
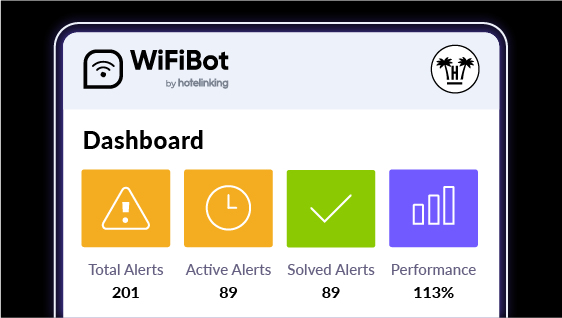
Stage four: establish advanced analytics and optimisation capabilities to continuously improve system performance and business outcomes.
The integration provides real-time dashboards with campaign capture, verification, and performance metrics. Automated processes eliminate duplicates, enrich data, and, through machine learning, adjust verification criteria to maintain an accurate and up-to-date database.
Most hotel groups need between 12 and 18 months to complete the four stages, with each phase delivering measurable improvements in data quality and marketing performance. The key to successful implementation lies in treating integration as an ongoing technical capability rather than a one-off project, with continuous optimisation based on performance metrics and business requirements.
Security and regulatory compliance in captive portal integration with PMS
The integration between the captive portal and the PMS introduces new security requirements that must be addressed from the design stage, with a robust architecture and well-defined operational controls. Involving the real-time transmission of guests’ personal information, this connection requires the use of encryption protocols and access control mechanisms that ensure data privacy without affecting system performance.
Technical security measures begin with the use of Transport Layer Security (TLS) encryption, which protects all API communications between the captive portal and the hotel’s PMS. Authentication protocols must verify the identity of each system and prevent unauthorised access to guest information, while logging mechanisms generate audit trails that facilitate regulatory compliance monitoring and security incident response.
In addition, the architecture must incorporate failover functions to ensure continuity of Wi-Fi access even if the connection to the PMS is temporarily interrupted.
GDPR compliance requires specific technical capabilities for managing consent and data subject rights. The system must record when and how guests consented to data collection and marketing communications, with granular controls that allow guests to specify their preferences for different types of communications.
Data retention policies must automatically archive or anonymise guest information in accordance with regulatory requirements, while providing mechanisms for guests to request the deletion or modification of data.
Implementation roadmap for hotel IT teams
Hotel technology teams planning to integrate their PMS with a captive portal should focus on three technical priorities. These actions lay the foundation for a successful implementation and generate measurable results in less than 90 days.
1. Audit the current infrastructure.
Conduct a comprehensive assessment of the Wi-Fi network and existing PMS to identify integration requirements and potential limitations.
The audit should analyse:
- API capabilities and documentation.
- Active security and authentication protocols.
- Performance and availability requirements.
- Current guest data collection processes and gaps that integration can address.
2. Automate guest validation from WiFi access.
Implement basic validation with the PMS to eliminate most access issues and lay the groundwork for advanced data collection.
This initial phase should focus on:
- Verifying guest identity upon connection.
- Managing errors and exceptions in the validation process.
- Monitoring performance to ensure WiFi access remains smooth.
3. Incorporate real-time email verification.
Enable automatic email validation at all guest data collection points.
This allows you to:
- Prevent erroneous or false data from entering marketing systems.
- Maintain campaign deliverability close to 99%.
- Reduce manual database cleaning and maintenance work.
Hotel groups that achieve 70% capture rates and 99% deliverability do not rely on proprietary technology or large budgets.
The secret lies in applying a systematic approach: treating guest data as a strategic asset, supported by robust architecture, security controls and well-designed operational processes.
The integration tools already exist; the real question is whether hotel chains are ready to leverage them and transform guest data into a sustainable competitive advantage.