Schedule 2 —
Technical and Organizational Security Measures
Marketing department
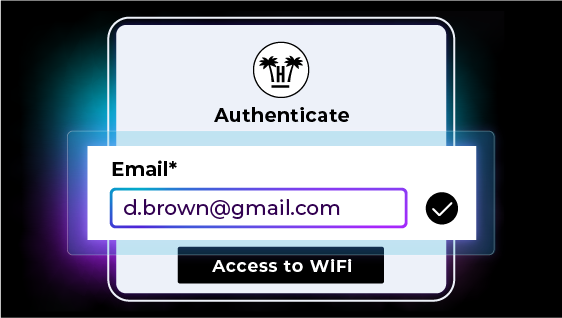 GuestMakerGuest Engagement Engine
GuestMakerGuest Engagement Engine
IT & Networks Department
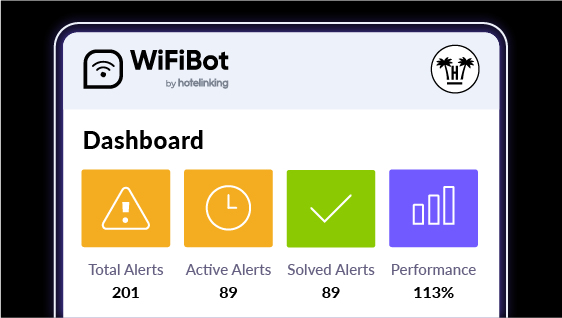 WiFiBotProactive Network Guardian
WiFiBotProactive Network Guardian
Operations Department
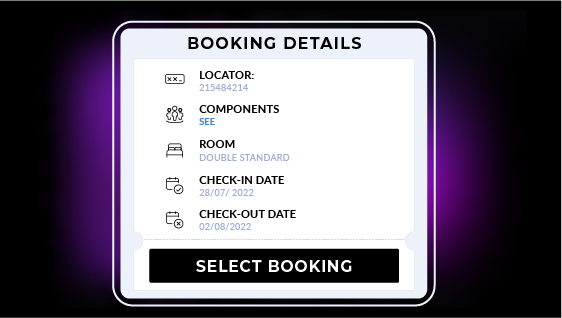 DeskForceFront Desk Automation System
DeskForceFront Desk Automation System
 Build High-Quality DatabasesA complete, top-tier database is crucial for driving direct bookings.
Build High-Quality DatabasesA complete, top-tier database is crucial for driving direct bookings. Customized Digital Check-In SolutionsOnline Check-In systems are leading the way in enhancing the guest experience.
Customized Digital Check-In SolutionsOnline Check-In systems are leading the way in enhancing the guest experience.Marketing department
 GuestMakerGuest Engagement Engine
GuestMakerGuest Engagement Engine
IT & Networks Department
 WiFiBotProactive Network Guardian
WiFiBotProactive Network Guardian
Operations Department
 DeskForceFront Desk Automation System
DeskForceFront Desk Automation System
 Build High-Quality DatabasesA complete, top-tier database is crucial for driving direct bookings.
Build High-Quality DatabasesA complete, top-tier database is crucial for driving direct bookings. Customized Digital Check-In SolutionsOnline Check-In systems are leading the way in enhancing the guest experience.
Customized Digital Check-In SolutionsOnline Check-In systems are leading the way in enhancing the guest experience.